Costa Rica declares national emergency after Conti ransomware attacks


Costa Rican President Rodrigo Chavez has declared a state of emergency following a series of cyberattacks by government against various government agencies.
BlippingComputer further noted that County Costa Rica posted most of the 672GB junk containing information from government agencies.
The statement was signed by Chavez on Sunday, May 8, the day the economist and former finance minister became the country's 49th and current president.
Costa Rica has declared a state of emergency following the cyber attack
On Sunday, May 8, Costa Rican President-elect Chavez Conte declared a state of emergency, citing ongoing ransomware attacks.
Conti Ransomware last month claimed a ransomware attack against Costa Rican government agencies.
The Costa Rica Social Protection Fund (CCSS), the country's public health agency, has previously stated that "the Conti Ransomware program tests security to verify and prevent potential attacks at the CCSS level."
Review the implementation of the Conti Ransomware Perimeter Review to verify and prevent CCSS.
- CCSSdeCostaRica (@CCSSdeCostaRica) April 19, 2022
BleepingComputer noted that the Conti data leak site was updated yesterday to report that the group had leaked 97% of 672GB of junk data, which allegedly contained information stolen from government agencies:
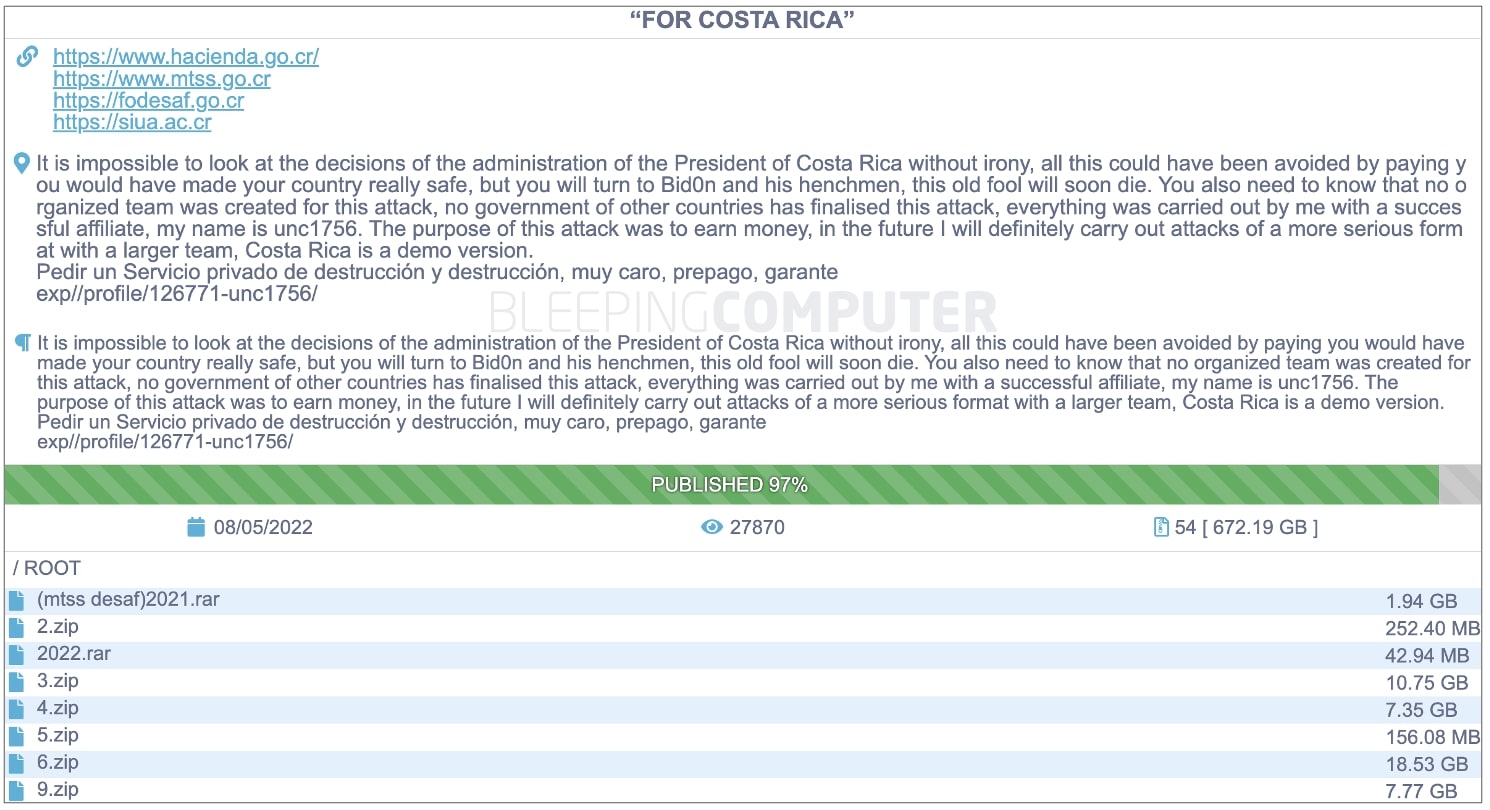
The first government agency to be hit by the County cyber attack was the Ministry of Finance, which has yet to fully assess the extent of the security incident or how it has affected information about taxpayers, system payments and customs.
Conti had earlier demanded a 10 million ransom from the ministry, which the government refused to pay .
The site leaked by Conti lists the following governments that will be affected by the attack, as currently seen by BleepingComputer:
- Costa Rican Ministry of Finance, Nazirio de Hasinda
- Ministry of Labor and Social Security, MTSS
- Funding for Social Development and Family Allowance, FODESAF
- Headquartered at Alazuile Inter University, SIUA
BlippingComputer has not yet analyzed the leaked data, but preliminary analysis of a very small fraction of the leaked data shows the source code and SQL databases visible on the official website.
Instead of blaming national state hackers for the cyber attack, Conti, the threatening actor UNC1756, along with their associates, took full responsibility. The horrific actor has threatened to launch "more serious" attacks in the future.
Amelia Rueda news agency reported that the executive order no. 42542, which previously reported development, created a state of emergency:
"Costa Rica's attack on cybercriminals and cyber terrorists has been declared a national emergency and we are signing this decree to declare a national emergency across Costa Rica's public sector and allow our society to respond. Attacks are criminal acts," the president said. Minister Natalia Diaz and Minister of Science, Innovation, Technology and Telecommunications (Micitt) Carlos Alvarado.
Amelia Rueda says digital treasury services have been inaccessible since April 18, violating official procedures, signatures and seals, affecting the entire "manufacturing sector".
"We have signed a decree to protect the country from criminal attacks by cybercriminals. It is an attack on our country and we have signed the decree to better protect ourselves," Chavez said.
Other organizations affected by Conte's attack include:
- Cartago Electric Service Commission (JSEC)
- Ministry of Science, Innovation, Technology and Telecommunications
- National Institute of Meteorology (IMN)
- Radiographic Costarisens (Racsa)
- Costa Rican Social Security Fund (CCSS).
As reported by BleepingComputer last week, the U.S. government is offering a reward of up to $ 15 million for information leading to the capture of ransomware management and the identification and arrest of operators.
The U.S. State Department has offered an additional 5 million to $ 10 million in rewards for information leading to the arrest and / or condemnation of the perpetrators of this attack.
The County Ransomware Group is under investigation
Konti is a Ransomware-as-a-Service (RaaS) operation linked to the Russian-speaking cybercriminal group Wizard Spider (also known for other notorious malware including Ryuk, TrickBot, and BazarLoader).
Among the victims of a gang of cybercriminals, the executive director of the Irish Health Service (HSE) and its health department (DOH) are the first to demand a 20 million ransom .
The FBI also warned in May 2021 that contingent operatives sought to disrupt many U.S. health and first aid agencies .
In August 2021, a disgruntled branch leaked Conty's training materials, which included information from an operator, various malware installation instructions, and many backup documents provided to the group's branches .
According to analysts at several cybersecurity firms, Conti now operates a variety of by-products to run ransomware operations or, if necessary, pay for major network access.
One such parallel operation is the recent information hacker group Karakurt, which has been active since at least June 2021 and has recently been linked to Conti as a hacking arm of a gang of cybercriminals by Advanced Intelligence, Infinitum, Arctic Wolf, Northwave and its researchers. On-chain analysis .